|
HTTPS
HTTPS is an encrypted version of HTTP implemented through the Secure
Socket Layer, SSL, standard. The encrypted secure connection is
created by running an ordinary HTTP connection on top of an encrypted
SSL connection. Except for this, HTTPS is like HTTP.
Creating a HTTPS port
To set up a HTTPS port you enter the protocol, HTTPS, and port number,
by default 443, as you would for an HTTP port. When you press the
Use these values button you will get two new options,
Certificate file and Key file. If your
certificate also contains your private RSA key you only need to fill
in the Certificate file option. Otherwise you will have to
fill in both options. The demo certificate included with Challenger
contains the private RSA key, while the certificates you get from a
Certificate Authority does not.
 It is not possible to run HTTPS IP-less. This is because the
certificate contains the name of the web site and the certificate is
used before the server gets a chance to see the Host header of the
HTTP protocol.
It is not possible to run HTTPS IP-less. This is because the
certificate contains the name of the web site and the certificate is
used before the server gets a chance to see the Host header of the
HTTP protocol.
Certificates
One fundamental property of secure communication is that you must be
certain whom you are communicating with. On the Internet you use
DNS to find a web server, but DNS is not secure. Therefore, you need
to be able to check that DNS really connected you to the right web
server.
This is done through certificates. A certificate is digitally
signed by a Certificate Authority, and contains information about the
web server. The browser can check that the information and the digital
signature are correct, as long as it knows about the Certificate
Authority that has issued the certificate.
In order to get a real certificate, you must first create a
certificate signing request and then send that request to a
Certificate Authority, who will then check that you are whom you claim
to be, and then give you a certificate that they have digitally
signed.
It is also possible to create your own self-signed certificates.
This goes against the whole idea of certificates, since they don't
really provide any added security. Therefore browsers will show a
warning dialog when they encounter a web site with a self-signed
certificate. But the self-signed certificate might do until you get a
real certificate.
Generating an RSA key pair
The certificates and digital signatures used are based upon public key
cryptography and the RSA algorithm. It essentially works by creating a
key pair, where one key can decrypt what the other key has encrypted.
One key in the pair becomes your public key that you give to the
world, the other key becomes your private key, which you keep secret.
This last thing, to key your private key secret, is important, for
anyone who has your private key can decrypt the traffic from your web
site, even though you are using HTTPS.
 You should consider running your secure web server on a machine with
few users and high security, to make it hard for others to get hold of
the private key. If you want many users to be able to modify the web
site, it is advisable to consider running an extra, separate server
for doing the HTTPS part. That server could then use the HTTP
Relay module to relay requests to the normal web server.
You should consider running your secure web server on a machine with
few users and high security, to make it hard for others to get hold of
the private key. If you want many users to be able to modify the web
site, it is advisable to consider running an extra, separate server
for doing the HTTPS part. That server could then use the HTTP
Relay module to relay requests to the normal web server.
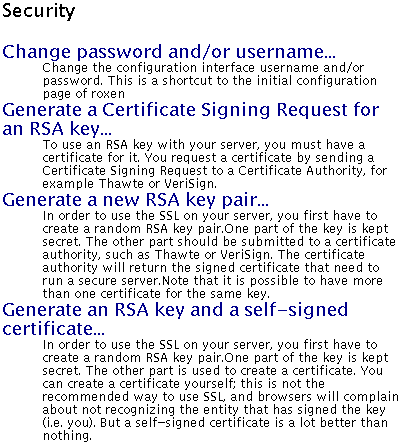
You can generate an RSA key pair with the Security/Generate
a new RSA key pair... action. You should keep on to the key
pair since you will need it later, after you get your signed
certificate.
Requesting and generating certificates
Creating a certificate signing request
The next step is to create a certificate signing request. This is done
through the Security/Generate a Certificate Signing Request
for an RSA key.... You will need an RSA key pair to
run this action. This action will prompt you for information about
your organization and your web site. When you have filled in all
information it will generate a standard certificate signing request
that you can send to a Certificate Authority, such as VeriSign or Thawte.
Creating a self-signed certificate
You create a self-signed certificate with the action
Security/Generate a RSA key and a self-signed
certificate.... It creates a RSA key file as well as a
certificate file.
Demo certificate
Included with Challenger is a demo certificate,
server/demo_certificate.pem. It will be used by the
installation script when installing a Challenger server which uses
HTTPS for its configuration port. It should however be changed as soon
as possible to a self-signed certificate, or even better a real
certificate. Since anybody that downloads Roxen Challenger gets the same
certificate, it is possible to eavesdrop on the encrypted traffic if
the demo certificate is used.
|